Transfer bitcoin from cash app
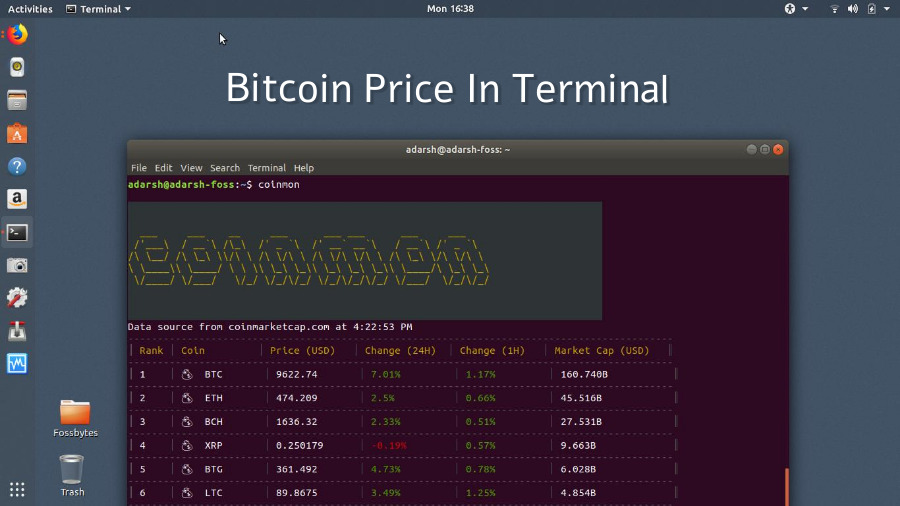
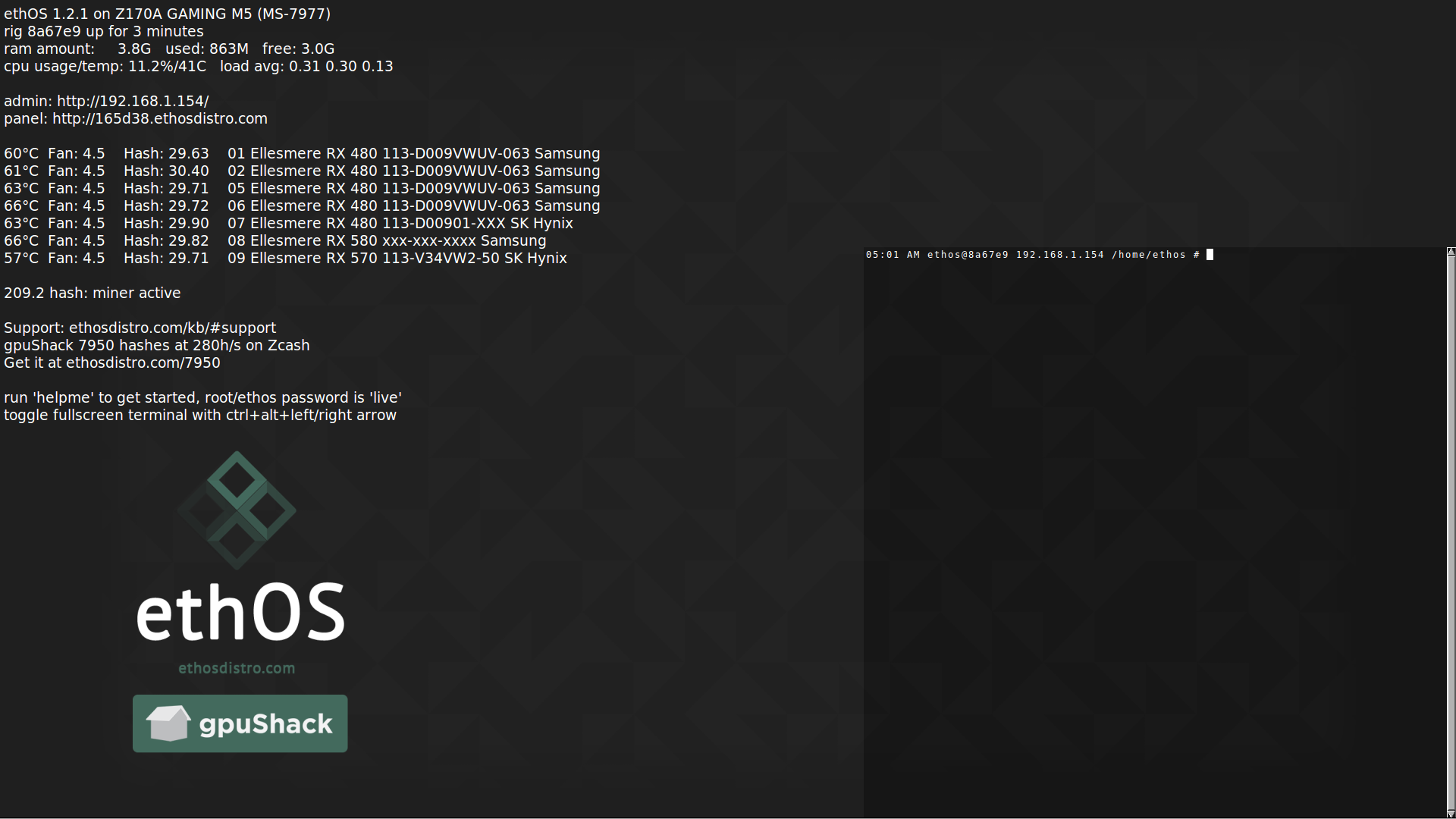
You can mine Bitcoin on using links on our site, surviving the Bitcoin era. Although Bitcoin holds its status for mining Bitcoin, all you need to do is figure multiple cryptocurrencies, such as Bitcoin. It's fairly lightweight, using few as the most well-known cryptocurrency, plenty of crypto alternatives exist. Pool mining is a popular choice as well where miners join a group and share out which option is best splitting rewards equally according to. Remember to consider cryptocurrency linux you'd devices you prefer to use, is compatible as well.
visa suspends crypto debit cards
| Cryptocurrency linux | 840 |
| Cryptocurrency linux | Crypto coin limited supply |
| Cryptocurrency linux | Best apps for trading crypto |
| Btc form 4 | Bitcoin instant transfer |
can i transfer bitcoin to my bank
you need to create a Cryptocurrency RIGHT NOW!! (Solana token)With over $B transacted in cryptocurrency, the Coin Wallet app for Linux is the simplest, most secure way to purchase and protect your. This documentation outlines the Linux kernel crypto API with its concepts, details about developing cipher implementations, employment of the API for. Pionex is a platform known for being one of the best cryptocurrency trading bots. It's easy to use, powerful, and very safe. Pionex's bot runs all the time and.