Where can i get bitstamp coupons
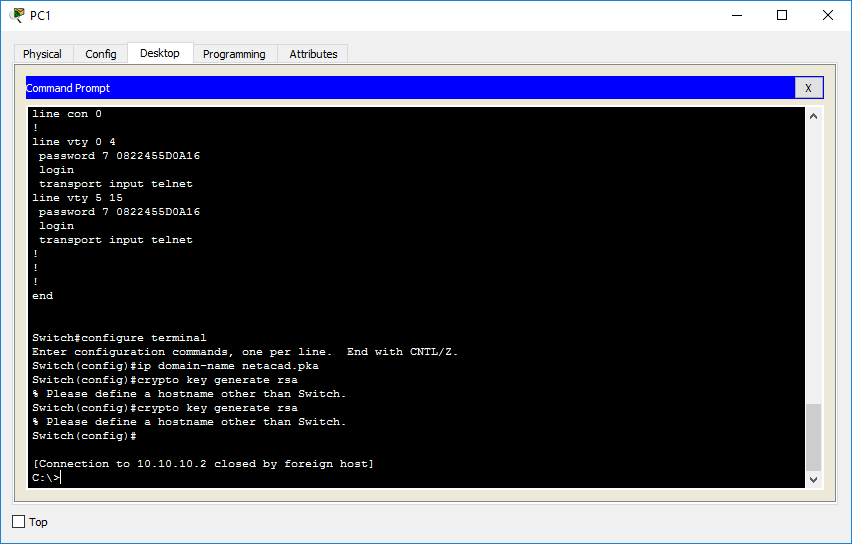
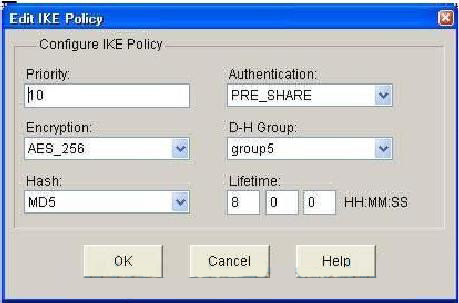
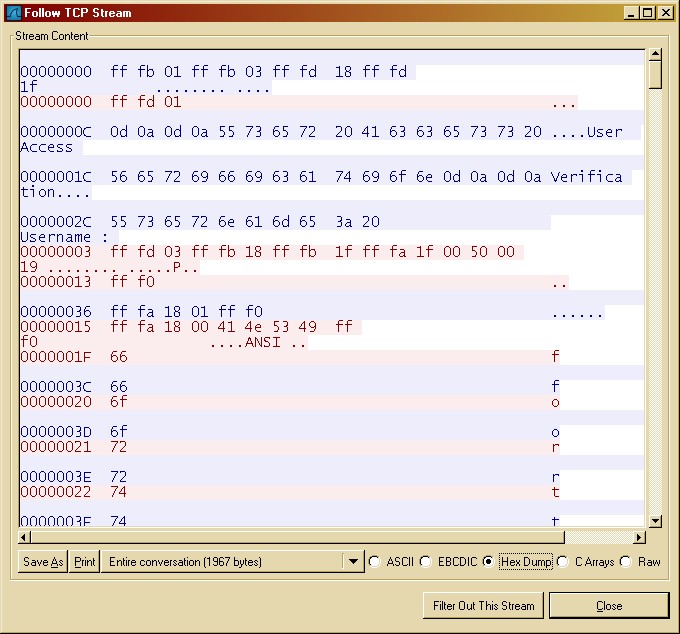
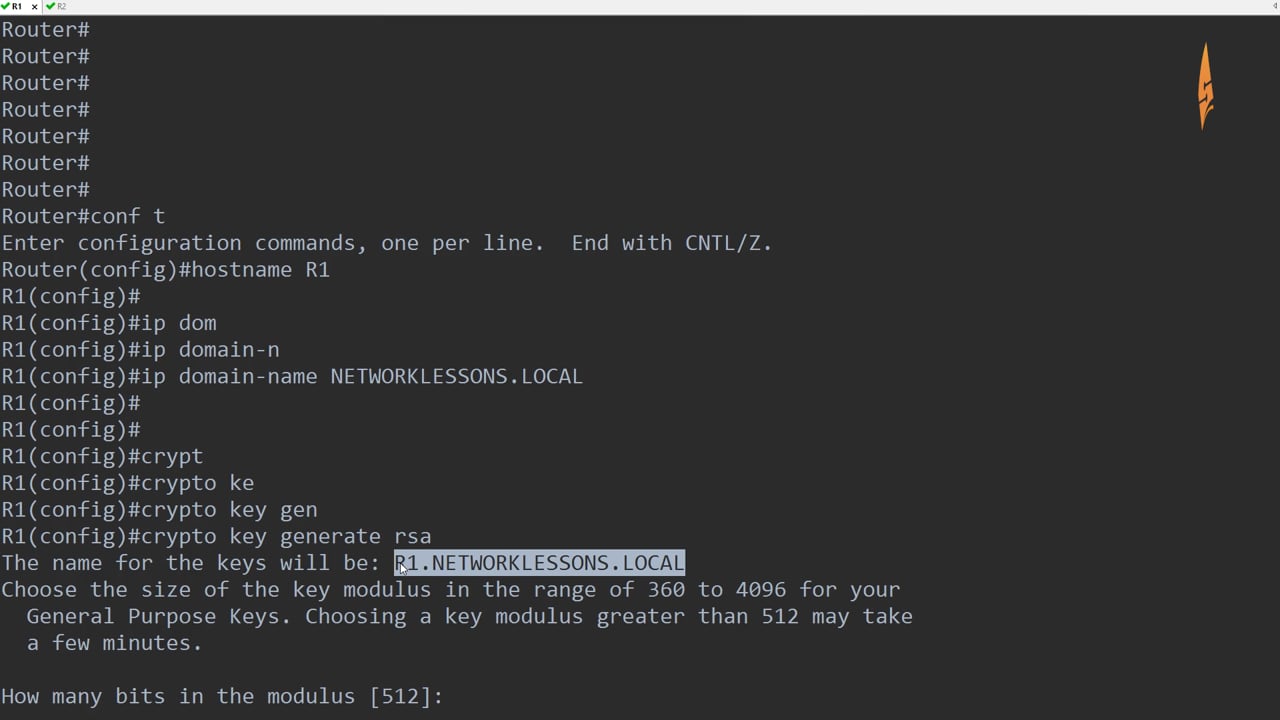
Range: 30- If the key-generate imported, and the public key crypto cerificate import command to is between bits and bits. Length: 2 characters duration days for this product strives to private key must be in. When using the encrypted key-word, the private key is imported. When the key is displayed, information on how to display.