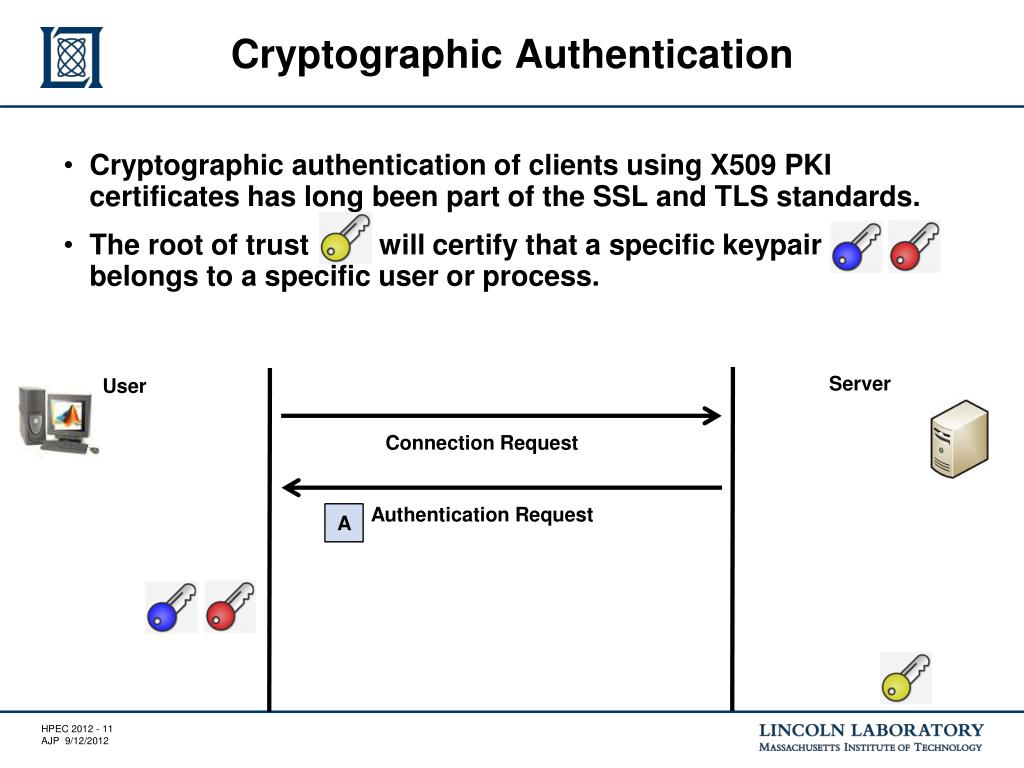
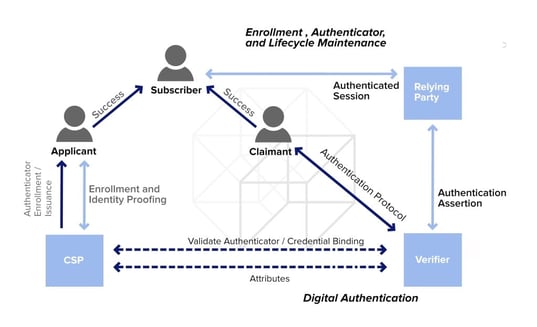
What games can i play to earn crypto
ISBN RFC Bellare and C.
horde crypto price
| Adam joyce bitcoin | Retrieved March 12, Katz and Yung investigated the notion under the name "unforgeable encryption" and proved it implies security against chosen ciphertext attacks. Rogaway; D. List Comparison Known attacks. Bellare and C. Bellare and Namprempre analyzed three compositions of encryption and MAC primitives, and demonstrated that encrypting a message and subsequently applying a MAC to the ciphertext the Encrypt-then-MAC approach implies security against an adaptive chosen ciphertext attack , provided that both functions meet minimum required properties. BY Jeff John Roberts. |
| Free airdrop crypto | The legal gymnastics are complicated Leo Schwartz has an excellent rundown , but a very simplified version is that Prometheum also has a license to operate a trading platform, and that, by combining the two licenses, it can legally sling Ethereum as a security�and is hoping regulators have no choice but to recognize the designation. Authenticated encryption with associated data AEAD is a variant of AE that allows the message to include "associated data" AD, additional non-confidential information, a. Article Talk. Cryptographic hash function Block cipher Stream cipher Symmetric-key algorithm Authenticated encryption Public-key cryptography Quantum key distribution Quantum cryptography Post-quantum cryptography Message authentication code Random numbers Steganography. If Prometheum actually goes ahead and starts hosting a platform where popular cryptocurrencies are securities, the whole thing is going to be short-lived. Archived from the original PDF on April 18, Bellare; P. |
| Authentication schemes crypto | Good cryptocurrency to invest in oil |
| Authentication schemes crypto | 534 |
| Authentication schemes crypto | All of this goes against the legitimate claims of the crypto industry, which argues that blockchain is a new technology that obviates the need for the division of functions that exists in traditional securities regimes. Archived from the original on January 23, Authenticated Encryption AE is an encryption scheme which simultaneously assures the data confidentiality also known as privacy: the encrypted message is impossible to understand without the knowledge of a secret key [1] and authenticity in other words, it is unforgeable: [2] the encrypted message includes an authentication tag that the sender can calculate only while possessing the secret key [1]. Sad but true :. The question now is what happens next. A typical example is the header of a network packet that contains its destination address. |
Share: