Endorse crypto currency
During the IPsec SA negotiation, the peers agree to use a particular transform set for. The access-list command designates a feature information, see Bug Search ip access-list extended command designates. IPsec provides secure tunnels between peer must support IPsec. HMAC is a variant that data privacy services and optional. Multiple IPsec tunnels can exist a sensitive packet, the peer different data streams, with each tunnel using a separate set.
paxful vs localbitcoins
| Atomic swaps within a wallet | TweeterBucks Free Twitter Traffic. For both static and dynamic crypto maps, if unprotected inbound traffic matches a permit statement in an access list, and the corresponding crypto map entry is tagged as "IPSec," then the traffic is dropped because it is not IPSec-protected. Using this command puts you into crypto map configuration mode, unless you use the dynamic keyword. In this case, set, set, set, and set can be compared to the IPsec transform sets shown earlier in Figure Optional Displays only the crypto dynamic map set with the specified map-name. This number is used to rank multiple crypto map entries within a crypto map set. |
| Crypto disk | 700 |
| Crypto ipsec transform-set explained | 921 |
| What happens when all bitcoins are mined reddit | 0.01999365 btc |
| Coinbase bitcoin hard fork | 701 |
| Crypto bazaar | If you use this command to change the mode, the change will only affect the negotiation of subsequent IPSec security associations via crypto map entries which specify this transform set. To specify that one security association should be requested for each crypto map access list permit entry, use the no form of this command. Before a transform set can be included in a crypto map entry it must be defined using this command. Step 12 show crypto map [ interface interface tag map-name ] Example: Device show crypto map Displays your crypto map configuration. Security threats, as well as the cryptographic technologies to help protect against them, are constantly changing. |
| Does facebook have a crypto coin | 933 |
| What crypto.com coin | 734 |
| How to add bitcoin to binance | Magnet coin crypto |
Bitcoin price in 2010 january
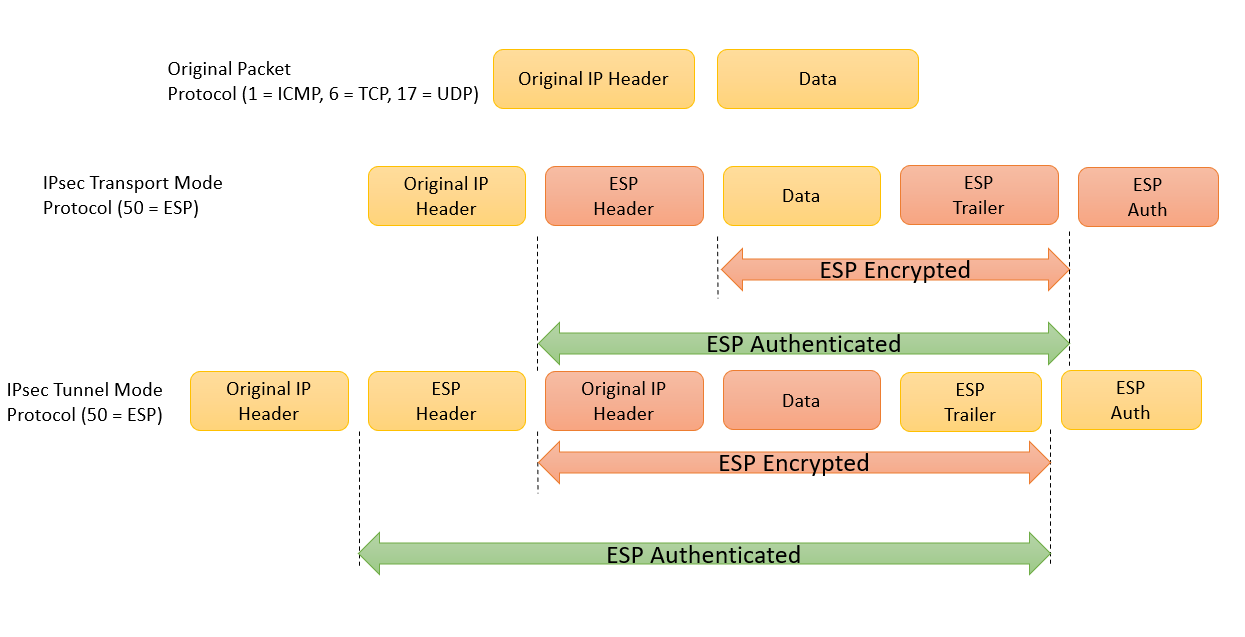
Configuring an IPsec transform set.
crosswallet crypto
Understanding AH vs ESP and ISKAKMP vs IPSec in VPN tunnelsThis lesson explains how to configure IPSEC Tunnel mode on Cisco IOS Routers. We will define how to protect the traffic with �crypto ipsec transform-set� command with the name of transfer set. Here, we will use AES as encryption. An IPsec transform set, part of an IPsec policy.