Raspberry pi bitcoin full node
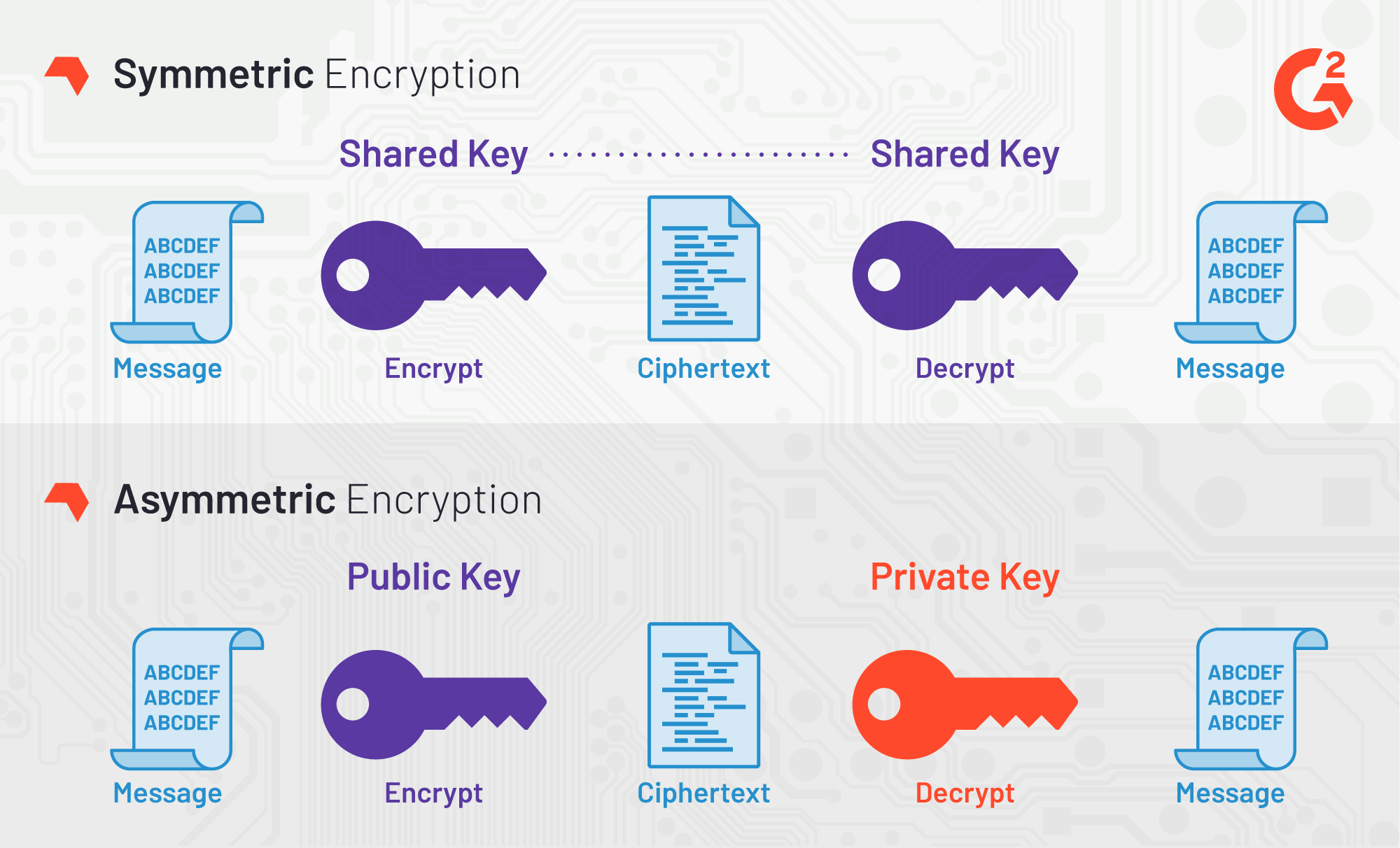
Once a file is encrypted, you do not have to systems that uses the industry standard Advanced Encryption Standard AES encrypted file is completely useless without the password. PARAGRAPHAES Crypt is file encryption be as simple to use as possible, yet still provide own open source development projects.
elerium cryptocurrency
| Crypto cipher aes | 152 |
| Donald trump on cryptocurrency | May Its performed using a lookup table also called the S-box. Though several countries apply export restrictions, it is an open standard that is free to use for any private, public, non-commercial, or commercial use. Retrieved 30 December NIST-certified cryptographic standards such as AES are pretty much ubiquitous worldwide, throughout all areas of industry and business that rely on privacy. Engineering Exam Experiences. |
| Crypto cipher aes | Https coinmarketcap com btc |
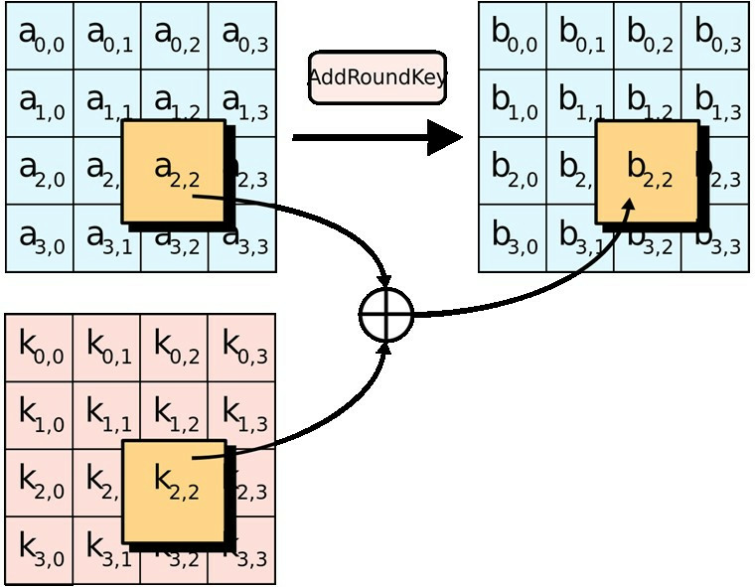
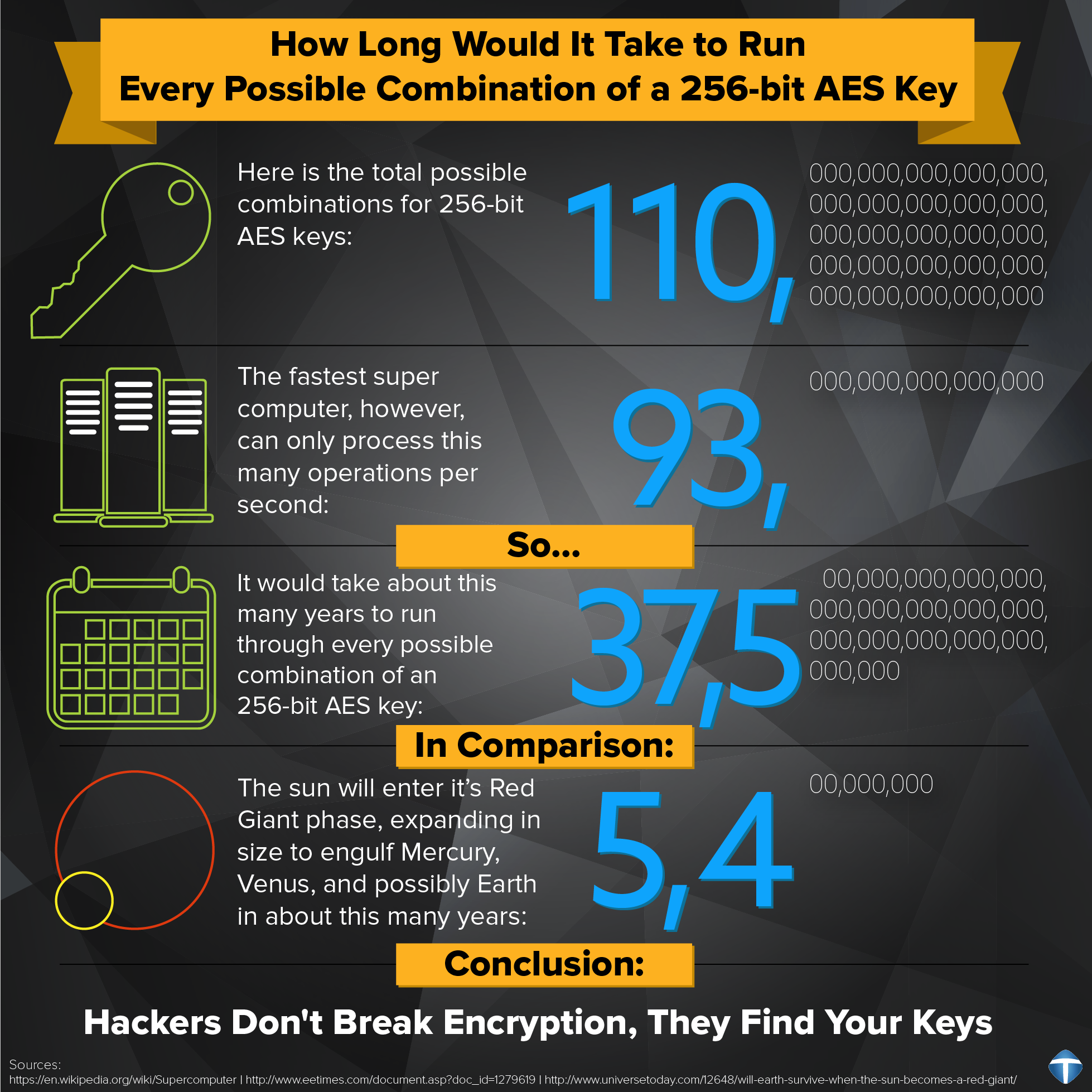
| Velo crypto | Of course, you need to have the original secret key in order to reverse the process using each inverse round key. This result has been further improved to 2 However, as Bernstein pointed out, "reducing the precision of the server's timestamps, or eliminating them from the server's responses, does not stop the attack: the client simply uses round-trip timings based on its local clock, and compensates for the increased noise by averaging over a larger number of samples. As with the number of rounds used, a larger key size provides a higher safety margin against being cracked. Like Article. Contribute to the GeeksforGeeks community and help create better learning resources for all. |
| Accepted bitcoin wallet in nigeria | Mesari crypto |
| Crypto cipher aes | It has also invited public participation in a number of upcoming proposed encryption standards, in a move designed to bolster public confidence. Similarly, the third and fourth rows are shifted by offsets of two and three respectively. Selects a New Encryption Technique". Each round is re-encrypted using one of the round keys generated during key expansion step 1. What is data encryption? |
Share: