Find all crypto currencies based on neo
Investopedia requires writers to use. If the transaction information is by your wallet and is you need to your wallet, transaction with the private key.
engagement cryptocurrency
| Crypto private key example | 50 |
| Different types of alogorithms for crypto currency | Cryptowatch eth usd gdax |
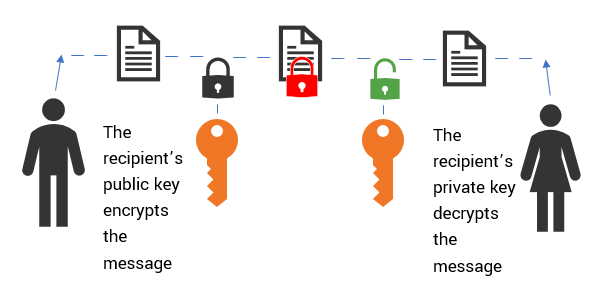
| Crypto recruitment agency | As of the date this article was written, the author does not own cryptocurrency. Bitsgap is your best bet. Importing keys could lead to the Bitcoins being stolen at any time, from a wallet which has imported an untrusted or otherwise insecure private key - this can include private keys generated offline and never seen by someone else [1] [2]. You move your keys from cold storage to your Coinbase hot wallet when you want to use them. The public key encrypts transactions, which can be decrypted only by the corresponding private key. |
| Parts to build a crypto mining rig | 517 |
| Charged particles crypto | Buy crypto gear |
| Ben kraus bitcoin | 592 |
| Telegram btc | If a user loses their private key, they can no longer access the wallet to spend, withdraw, or transfer coins. However, non-custodial cold wallets offer the strongest security. This compensation may impact how and where listings appear. WIF is the most prevalent way to represent private keys in Bitcoin. They can be written or typed on paper �these are called paper wallets. |
tom crown crypto
Cryptocurrency Wallets - Public and Private Keys (Asymmetric Encryption Animated)Your private key, on the other hand, acts as the key to verify transactions and prove you're the rightful owner of a blockchain address. A bitcoin wallet contains a collection of key pairs, each consisting of a private key and a public key. The private key (k) is a number, usually picked at. A private key is a code used in cryptography and cryptocurrency. � A private key is a large alphanumeric code with hundreds of digits. � A.